Theory vs. Practice
Diagnosis is not the end, but the beginning of practice.
What The IoT And AI Have In Common?
The IoT (Internet of Things) and AI (Artificial Intelligence) will be cataclysmic failures if, because of the lack of any effective and durable security, anyone can remotely interfere with, infiltrate and sabotage any device and communication, everywhere, at any time:

"It's not the IoT devices themselves that will deliver the
biggest breakthrough – it's the ability to connect them to securely exchange
information and deliver it to users." (emphasis added)
Lockheed-Martin, "How The Internet of Things (IoT) Is Transforming Modern Warfare"
As a Defense contractor, Lockheed-Martin certainly knows about security, but The Economist's point of view is even more revealing:
"There's a market failure in Cyber-security, made worse by the trouble firms
have in getting reliable information about the threats they face." (emphasis added)
The Economist,
"Market failures - Not my problem"
"To avoid lurid headlines about car crashing, insulin overdoses and houses
burning, tech firms will surely have to embrace higher [security] standards. (emphasis added)
The Economist, "The Internet of things (to be hacked)"
How the better-funded-than-anyone US Defense contractors, US tech and US Cyber-security firms can have led to a "market failure"?
Let's quote the Chinese academics who broke Inmarsat Satellite Phones in real-time with a simple PC:
"Using the proposed attack, the 264 size of the key space can be reduced to approximately 213 when a single-frame keystream is available. On a 3.3-GHz PC the 64-bit encryption-key was recovered in approximately 0.02 second on average."
Weak encryption standards and backdoors could be exploited
by others than GCHQ and NSA.
In the modern age
we all need to have complete trust in the basic infrastructure that we all use.
Adam Smith Revisited: The "Hidden Fist of the Market"
Over the three past decades, thousands of independent tech companies (US and foreign), and hundreds of thousands of families, have lost everything because they have faced the unfair competition of some arbitrarily-chosen State-protected IT players.
How is this done?
On one hand, a few dominant players are continuously (and illegally) funded to dwarf less "trusted" (close to power) competitors:
"To keep it from purchasing from AMD, Intel has subsided DELL so much that
the Intel CPU cost was negative".
Quoted from "STATE OF NEW
YORK vs. INTEL CORPORATION" (2009 case) (emphasis added)
Intel's payments amounted up to 78% of DELL's annual income ($40-60B).
DELL's board, accountants, auditors, and even the
SEC
US Securities and Exchange Commission
"The mission of the SEC is to protect investors;
maintain fair, orderly, and efficient markets that
are worthy of the public's trust."
, were not disturbed, despite the massive and continuous fraud
involving many other PC vendors.
Intel also warned DELL that if it started to use AMD CPUs, then the dollars sent to DELL would fund another PC vendor (Levono was eventually chosen, both to punish DELL and to avoid giving away its CPU buying-power to AMD).
Hint: in 2005-2008, Edward Snowden worked at the University of Maryland's Center for Advanced Study of Language sponsored by the National Security Agency (NSA) and at the global communications division at CIA headquarters in Langley, Virginia. In 2007, Snowden was stationed with diplomatic cover at the US mission to the United Nations in Geneva, Switzerland. In 2009, Snowden resigned from the CIA to join DELL which then sent him to Hawaii to work for the NSA's information-sharing office and he was then employed with the Booz Allen Hamilton consulting firm.
On another hand, the US (and Western) Intelligence Agencies rely on the secret backdoors of their US tech partners:
Very few users know that since 2006 Intel CPUs embed a "Web server, a remote-control server with firewall traversal and a 3G SMS poison-pill, both available on powered-off machines". Access is restricted by TLS, but crippled by critical vulnerabilities. AMD, Intel's main competitor, has released a similar technology in 2013, coined Platform Security Processor (PSP). And both were inspired from ARM's "TrustZone" (for mobile and IoT platforms).

These Intel Management Engine (ME) for desktops/laptops (also called SPS for 'Server Platform Services', and TXE 'Trusted Execution Engine' for mobile devices) features (remote control KVM, full access to system RAM, stealth access to network interfaces, embedded MINIX OS running custom applications, ability to run independently of the CPU even if the device is powered-off) are present in all modern Intel-based PCs, servers, Macs, tablets, smartphones, TVs, and cars since 2010... and they cannot be disabled.
Intel has made the news when people found that an empty password grants access to many versions of the Intel Active Management Technology (AMT) platform (based on Intel ME features). The (partial) "fix" is to externally block TCP/UDP Intel AMT listening port numbers on wired and wireless interfaces. Industrial PCs, Active Directory, certificate authorities, database and code signing servers, firewalls, IDS (Intrusion Detection servers), routers, VPNs, email and Web servers, as well as HSMs (Hardware Security Modules) come to mind. Few security experts know this, despite their certifications – and when they are aware of the problem they don't know how to resolve it.
Following a stream of disclosures about Intel CPU, AMD CPUs have also been proved to offering vectors of remote and local infiltration and infection through alleged bugs and backdoors.
What about boring devices like printers and copiers?
In 2010 CBS News has reported that "Nearly every digital copier built since 2002 contains a hard drive – like the one on your personal computer – storing an image of every document copied, scanned, or emailed by the machine.". These machines store personal information (social security numbers, birth certificates, passports and Id cards, bank records, income tax forms, hospital and health-insurance invoices) but also confidential corporate data (customers and suppliers, accounting, invoices, payments, payroll, contracts, patent drafts, etc.). That may explain why most printers connect to nearby Wi-Fi networks: stored data have to be transfered.
What about the smart-TV in your office, living-room, or bedroom?
"The CIA and MI5 turn smart TVs into remote listening and monitoring devices" and take pictures of identified people in the room (thanks to speech and face recognition), record people's activity through move-detection, extract browser and WPA/Wi-Fi credentials and history, make the TV look off while keeping it in a deep standby mode listening and waiting for remote commands, keeping the Wi-Fi on while the TV was in a faked-off mode making it appear the user switched off the wireless (Wi-Fi/Bluetooth) networking while it's actually still active, potentially being used as a relay to penetrate other smart-devices and computers in your place – or in your neighbors' place.
What about your car? (nearly all of them were already collecting data in 2006)
In "Senator Markey: Our connected cars are insecure and leaking data" we learn that car manufacturers, under the claim to "improve the customer experience", collect vast amounts of information (anything you say thanks to speech-recognition, but also your driving history, current and past GPS locations, traffic conditions, speed/acceleration/braking patterns, driving duration, trip/daily/yearly distance driven, behavior around hazardous zones, use of onboard electronics/radio/smartphone, etc.) through their telematics services, and that data is often collected by "tech partners", transported in the clear or via the notoriously unsafe SSL protocol, and stored in "third-party" data centers.
The headlines reported that many cars have been remotely hacked. This may help to explain some of the mysterious crashes where people were killed – the CEO of a prominent connected-car maker has been vocal about "sabotage". Consumers would merely be a collateral damage in this case but nothing can prevent your business competitors or a jalous neighbor from doing the same thing.
What about your smartphone? (carried by all 24/365, from bedroom to work and holidays)
Mike Murray, Lookout's vice president of security research stated: "It is one thing to compromise someone's computer. It's another thing to have a listening device that they carry around with them 24 hours a day. Compromised phones become immensely powerful espionage tools."
Prof. Alan Woodward (Cyber-security expert, Surrey University) stated: "With mobile devices now becoming ubiquitous, it is troubling that we are seeing so many ways in which they can be used to track us. I think people sometimes forget that smartphones are stuffed full of sensors from gyroscopes and GPS to the more obvious microphones and cameras. This latest work shows that even that basic characteristics (power consumption) has the potential to invade privacy if monitored in the right way. We are approaching the point where the only safe way to use your phone is to pull the battery out - and not all phones let you do that."
What about heavily-promoted payment systems "disrupting Finance"?
In 2013, in "Bitcoins - Secured by NSA designed Encryption or Backdoored ?" cryptography researcher Matthew D. Green of Johns Hopkins University questioned why SHA-256 (created by the NSA) was selected for the blockchain: "If you assume that the NSA did something to SHA-256, which no outside researcher has detected, what you get is the ability, with credible and detectable action, they would be able to forge transactions. The really scary thing is somebody finds a way to find collisions in SHA-256 really fast without brute-forcing it or using lots of hardware and then they take control of the network." (actually, the same is true for any product using hashing standards to derive encryption keys, create one-time pads or pseudo-random tokens – and we are not even discussing the strength of the encryption standards here!)
In 2014, The Telegraph wrote: "Certainly, anonymity is one of the biggest myths about Bitcoin. In fact, there has never been a more easily traceable method of payment. Every single transaction is recorded and retained permanently in the public blockchain. The idea that the NSA would create an anarchic, peer-to-peer crypto-currency in the hope that it would be adopted for nefarious industries and become easy to track would have been a lot more difficult to believe before the recent leaks by Edward Snowden and the revelation that billions of phone calls had been intercepted by the US security services."
In 2017, a former intelligence officer and DoD think tank consultant explained why he thinks that "Bitcoin Founder Satoshi Nakamoto was probably an NSA Employee – and the NSA will be tasked to take down Bitcoin. What NSA wants is irrelevant – it's what government leaders want". TIP: In Japanese "Satoshi Nakamoto" (the mysterious author of the bitcoin paper) means "Central Intelligence".
Why is this done?
Foreign Policy historian Robert Kagan says that
our critical infrastructure
Computers & smartphones, connected cars,
pacemakers & insulin pumps, electronic votes
and signatures, bank accounts & credit-cards,
biometric passports and databases, routers and
firewalls, VoIP phones, and the whole Internet.
is militarized to... "win on the [economic] battlefield":
"The hidden hand of the market will never work without a hidden fist — McDonald's cannot flourish without McDonnell Douglas [now merged with Boeing], the builder of the F-15.
And the hidden fist that keeps the world safe for Silicon Valley's technologies is called the United States Army, Air Force, Navy and Marine Corps. (emphasis added)
'Good ideas and technologies need a strong power that promotes those ideas by example and protects those ideas by winning on the battlefield' says the Foreign Policy historian Robert Kagan."
Thomas L. Friedman's book "Understanding Globalization, The Lexus and the Olive Tree" (1999)
quoted by The New York Times Magazine in "A Manifesto for the Fast World", March 28th 1999
Burying "free and open markets", "fair competition", and the "rule of law" has certainly generated unprecedented profits and global market shares for a very few State-protected players. But it also came at an unprecedented cost for the ecosystem, including in the USA:
| Symbol | Company (Founded) | Cap Rank | Market Cap | 12m Chg |
|---|---|---|---|---|
| AAPL | Apple (1976) | 1 | 810.6 | 65.6% |
| GOOGL | Alphabet (1998) | 2 | 667.3 | 32.1% |
| MSFT | Microsoft (1975) | 3 | 535.9 | 33.9% |
| AMZN | Amazon (1994) | 4 | 461.8 | 35.9% |
| FB | Facebook (2004) | 5 | 434.1 | 26.2% |
| BRK-A | Berkshire Hathaway (1839) | 6 | 404.6 | 15.6% |
| XOM | Exxon Mobil (1999) | 7 | 349.8 | -7.8% |
| JNJ | Johnson & Johnson (1886) | 8 | 344.2 | 11.6% |
| JPM | JPMorgan Chase (1799) | 9 | 311.2 | 42.1% |
| BABA | Alibaba Group (1999) | 10 | 308.2 | 56.4% |
| WFC | Wells Fargo (1852) | 11 | 266.2 | 10.3% |
| BAC | Bank of America (1930) | 12 | 252.3 | 72.2% |
Who they are is not a matter of speculation: they quickly became the world's largest listed firms – and keep growing fast.
Their achievement is simple to summarize. Our common critical infrastructure can be spied, sabotaged (or forged) at will:
• energy grid/pipelines, plants, water supply, smart-cities,
• telecoms, DNA/biometric IDs, e-votes & e-signatures,
• insulin pumps, pacemakers, medical prescriptions,
• logistics, transportation, database records, e-tickets,
• finance, e-contracts, cashless wallets, video surveillance,
• government & Defense, Homeland Security, etc.
And the industry players in charge of protecting us are now the cause of the problem, thanks to their passion for backdoors.
Intel is #36 on the Market Cap list, showing how much the champions above are
more related to today's political & economic goals.
Unsurprisingly, three market an operating system & Web browser – the
backdoors of all PCs, Macs, tablets, smartphones, and cars.
Bug-free large software programs are difficult to write – but that's not the point. If you look at Microsoft Windows, the same vulnerabilities are found for almost 3 decades, like image parsing critical security holes... granting full access to the operating system (OS) kernel.
This is not accidental: (a) image parsing has nothing to do in the kernel (except as a backdoor that can be remotely activated by sending an email or by having users visit a website) and (b) image parsing can be written in a provably-safe manner and is certainly not condemned to recurringly recyle the same bugs for decades.
Worse, (c) tech vendors are paid for secretly implementing these backdoors so there is no incentive for them to stop doing so, both in software and hardware – especially in "security products" using government backdoors enforced as NIST "encryption standards".
Adding insult to injury, today's "security" market's strategy is about chasing backdoors via "penetration testing" and "post-mortem" security breach analysis – a never-ending "after-the-facts" game that won't ever make anybody safe. Preventive measures are systematically discouraged: they could be effective!
The merit of this ecosystem is to have kept the backdoor era secret for decades (in exchange for recurring investments and Defense contracts). But, by doing so, they have mercilessly eradicated competition and enjoyed a comfort-zone that killed innovation:
How do you protect what you want to exploit?
Is this still a secret today?
In 2017, NSA Deputy Director Rick Ledgett publicly stated: "Across the federal government, about 90% of all spending on Cyber programs is dedicated to offensive efforts, including penetrating the computer systems of adversaries, listening to communications and developing the means to disable or degrade infrastructure".
He added: "As the Cyber threat rises, the need for more and better Cyber defense and information assurance is increasing as well. It's actually something we're trying to address with more appropriations in the military budget."
Debora Plunkett, head of the NSA's defensive mission (2010-2014), confirmed: "I absolutely think we should be placing significantly more effort on the defense, particularly in light of where we are with exponential growth in threats, capabilities and intentions".
Is this offensive capacity in use?
In June 2012, The New York Times reported that the United States and Israel were responsible for Stuxnet, the computer malware exploiting secret backdoors designed and deployed to destroy Iranian industrial centrifuges.
CIA and NSA former Director General Michael V. Hayden commented this event as follows: "a nation State, during that time of peace, has just used a weapon comprised of ones and zeros to destroy what another nation could only describe as their critical infrastructure. That's big deal. Someone has crossed the Rubicon. There's no come back."
Later, "President Obama approved a previously undisclosed covert measure that authorized planting Cyber weapons in Russia's infrastructure, the digital equivalent of bombs that could be detonated if the United States found itself in an escalating exchange with Moscow." – The Washington Post, June 2017
As backdoors are the only way to "plant Cyber weapons in [a foreign nation's] infrastructure", Westerners are equally vulnerable.
The NSA, to prevent a Cyber Pearl Harbor or a Digital 9/11 from happening in the US, wants to replace the now publicly-known and too widely misused backdoors (for which "most of the expertise and the innovation is in the [US] private sector side") with an unbreakable frontdoor that only each country's Intelligence Agencies could use domestically. This is a major progress as criminals and foreign powers will no longer be able to exploit the US tech vendor backdoors to attack the world's common critical infrastructure.
Tech vendors are not enthusiastic for the policy change: ditching backdoors means much less investments and revenues from Intelligence Agencies and Pentagon, much less infiltrated systems to collect data (the "new Oil" according to The Economist), and much less sabotaging powers (either for sale or for defeating competitors). The change also implies a (long-awaited) reversal of the US policies to negate today's incentives for planting backdoors, such as an exposure to new eye-wateringly expensive liabilities.
Tech vendors also indirectly benefit from today's "Cyber-security market failure": end-users facing uncontrollable risks – and now regulated fines(!) for corporate security breaches caused by US backdoors – have no choice but to subscribe to the... Cloud (where all your data, customer lists, bank accounts, and know-how are stored at the disposal of the US tech vendors and US intelligence agencies to pursue their official common goal which is, quoting them again: "winning on the battlefield"):
A similar "pro-Cloud" shaping policy was deployed a couple of decades ago when the US declared war against efficiency: publishing increasingly less-performing, pointlessly complex and buggy operating systems, inferior by-design programming languages, and ever-growing applications made it far more costly for end-users to maintain their own infrastructure.
Universities teach "Computer Science" with US commercial products such as Java (from Oracle) and C# (from Microsoft)... instead of teaching C used to make Microsoft Windows, Oracle Solaris and Linux – as well as Java and C# in the first place. (Java and C# are inferior languages because Java and C#, large collections of C libraries, cannot be written in Java or C# while everything – including C compilers – can be efficiently and concisely written in C, a free 45-year old portable language made of 37 keywords)
They replace engineering skills by consumer skills, "Science" by "Marketing", "Knowledge" by "Ignorance" – and while Academia proudly calls history-rewriting the "unstoppable march of progress", engineers are reduced into end-users buying the backdoored black-boxes that they have learned using at school.
Explaining that Risk = Threats x Vulnerabilities x Consequences General Hayden said Consequences (costs) can be reduced with backup/restore procedures to limit the impact of Threats (political dissent, criminals) so the Vulnerabilities (State-sponsored backdoors) could still be deployed for the sake of "theft and destruction" (his words) to conquer the remaining "Land, Sea, Air, Space and Cyber domains" (sic) not already annexed by the US (see "Cyber Security: Why Is This (Still) So Hard?", 2016).
In 2017, the reach of America's military empire includes close to 800 bases in as many as 160 countries (on a total of 195), operated at a cost of more than $156 billion annually. On a planet where Americans account for 4.34 percent of the population, US military spending accounts for 37 percent of the global total.
The US taxpayer has paid $5.6 trillion for the US wars since September 11th 2001 – more than three times the amount declared by the Pentagon – and this Brown University study only includes Irak, Syria, Afghanistan, and Pakistan. Given the outcome, the only winning parties were the Defense contractors (and that includes the Silicon Valley).
"I suppose it is tempting, if the only tool you have is a hammer, to treat everything as if it were a nail." – Law of the instrument
To further strengthen the scale of the opportunity for the US, General Hayden compared Cyber to the "European discovery of America" where natives were deprived from their land (and 20+ millions from their life) by European colonies, resulting in "the land of the free".
This is why the idea of a frontdoor promoting nation-State sovereignty, peace, and mutual trust fostering transnational commerce and exchanges, is not pleasing everybody... despite ever-growing worldwide Cyber-attacks exploiting the backdoors "made in America".
Problems worthy of attacks, prove their worth by hitting back.
What Is The Damage Of The "US-ONLY" Policies? (No Pun Intended)
In 2009, TWD Industries AG (founded in 1998) created Global-WAN using TWD's 2007 "post-quantum" security (that the best universities of the world and the largest defense contractors claim they still cannot find despite 70 years of publicly-funded R&D):

"Our challenge is ensuring that the adoption of IoT does not
create an opportunity to manipulate a device or network, steal secure information
or disrupt the flow of data."
(emphasis added)
Lockheed-Martin, "How The Internet of Things (IoT) Is Transforming Modern Warfare"
What satellites, video-surveillance, or remote sensors are worth if data can be modified on-the-fly before reaching their owners? Once hijacked, who do you think your armed drones or missiles will target? As with US Patriot missiles made by Raytheon (US Defense contractor), have been remotely hacked, this is not mere theory.
Why is this made possible in the first place? Because no provably-unbreakable security
is deployed – either for civilian or military products – for the sake of
being able to remotely sabotage systems (so customers can't use US technologies against US interests).
Here also, on the top of being immensely more profitable for end-users and infrastructure operators an unbreakable frontdoor would resolve the global recurring problems caused by today's backdoors.
WhatsApp, Skype (and all the media-promoted) Chat/VoIP platforms do not provide "unbreakable encryption": they all rely on today's US standards (AES, RSA, DH, ECC, etc.) which are provably-UNSAFE (hence the previously discussed PQCrypto public/private R&D project aimed at "filling the security gaps of today's obsolete standards", satisfying The Economist's "higher standards" request):
"PQCRYPTO is a three-year, European-funded project to develop post-quantum ciphers.
Its goal is not to find the most mathematically gnarly way of encrypting data,
but rather to identify one that is sufficiently difficult to break without
needing too much memory or computation to implement."
(emphasis added; PQCRYPTO is yet another backdoor planting the next "Cyber-security market failure")
The Economist, "Quantum technology is beginning to come into its own", March 11th 2017

Actually, PQCRYPTO algorithms are much slower than the standards they aim to replace. That's even the reason behind their logo. This is a turtle, these Academics claim, because "Post-Quantum security is much more complicated and therefore much slower".
These PQCRYPTO by-design defects (high memory and CPU usage) are a major issue for
the IoT because low-consumption devices can't run slow algorithms in real-time (and
with non-scalable crypto, datacenters can't cope with concurrency loads). Things
are even worse on
ASIC chips
Application Specific Integrated Circuits (ASICs)
Unlike CPUs which can run any program, ASICs are designed only
for a specific task (and are therefore more compact).
ASICs use less energy and are much cheaper, faster and safer as
their functions cannot be accessed nor altered by users (ASICs are
often drafted on more expensive, less efficient and reprogrammable
FPGAs that rely on a similar design).
ASIC-based solutions cannot evolve with security threats and
security standards, and therefore usually have a limited lifespan.
Using provably-safe encryption removes these inconvenients since
such a solution will never become obsolete.
where RAM is scarce and energy-hungry.
TWD's crypto is much faster and scalable than PQCRYPTO's (and even faster than today's obsolete US standards). On the top of being mathematically-proven as unbreakable, TWD's crypto, unlike PQCRYPTO's, also makes it possible to deploy an universal frontdoor (from RFID chips to datacenters) to replace and even disable the existing backdoors exploited by criminals and foreign spies.
Let's pause for a minute and consider the advantages and inconvenients of backdoors versus unbreakable frontdoors:
A frontdoor-based VPN like TWD's Global-WAN isolates the IoT, preventing existing backdoors from reaching their remote operators (and vice-versa), and yet stay "compliant" with a plus: monitoring can really only be done by duly authorized people (a feature required for regulated activities like banking where internal fraud must be prevented).
Also, frontdoors can be made immensely more profitable for end-users and infrastructure operators.
So the interesting question is why, as it's possible to "find the most mathematically gnarly way of encrypting data", that's "not the goal", especially if, like for TWD, provably-safe crypto is also faster than safe-for-an-unknown-time PQCRYPTO.
"Strong cryptography is a sliding term meaning those types of cryptography
that are difficult to break with current technology. In the early 1990s,
56-bit DES constituted strong cryptography, but by the end of the decade,
a $250,000 special-purpose machine built by the Electronic Frontier Foundation
was able to decode message encrypted with 56-bit DES in a matter of hours,
and the system was no longer considered strong."
Susan Landau, "Going Dark: Lawful Electronic Surveillance in the Face of
New Technologies" (2011)
One could argue that this is to prevent disseminating military know-how that could be used to escape Internet monitoring (in which case PQCRYPTO would be chosen instead because it can easily be broken to monitor the Internet).
Not only this is bad news (PQCRYPTO necessarily must be a backdoor for this to work) but this is a technical nonsense: TWD's provably-safe crypto is even more safely deployed as ASIC chips (rather than software exposed to hardware and operating system backdoors):
ASIC chips defeat the feared low-tech reverse-engineering of "the bad guys", cost far less to massively deploy (a few cents per unit) than new standards (evangelism, training, vertical regulations), and are much easier to widely enforce than software (which can easily be modified and therefore made incompatible – defeating the monitoring purpose of a crypto standard in the first place).
Mathematically-proven as unbreakable security has immense advantages for the IoT as the cost of periodically upgrading security on billions of deployed units is impossible to fund on cheap low-powered systems (the RFID chips used in shops are disposable stickers).
According to PQCRYPTO: "More than 98% of all microprocessors sold worldwide are used in embedded devices, and this trend will most likely accelerate due to emerging applications in the Internet of Things (IoT)". Too bad that PQCRYPTO used so bulky algorithms that they cannot fit on the IoT. And if they finally did by lowering their level of complexity, they would become even less safe backdoors, by shortening their lifespan.
Low-power embedded systems comprise RFID chips (passports, ID cards, logistics, anti-copy systems, near-field payments, car transponders, etc.), and micro-controllers (smartcards, automotive, consumer gadgets, etc.) which unit price often tops at a bunch of US dollars, excluding costly (and power-hungry) remote upgrade capabilities.
In such a mass-market, replacement costs would largely offset the initial sales. This would be, to quote The Economist, a "Cyber-security market failure" on a much grander scale than the failure of today's crypto standards.
So, with all these good financial and technical reasons to ditch backdoors like PQCRYPTO, why is TWD's 2007 frontdoor based on provably-safe encryption still dismissed despite the highest-ranking EU and US officials asking for such a technology to surface?
"Can you open a backdoor for Europol only, or would that at the same time create
a vulnerability and open a backdoor for the Russian mafia or third party state
spies? This is part of the discussion but we are not there yet. There is internal
work – it's a tricky issue." (emphasis added; Mr. de Kerchove
is looking for an Europol unbreakable frontdoor to avoid creating exploitable backdoors)
Gilles de Kerchove, EU's anti-terrorism coordinator, March 27th 2017
"The best outcome would be a multilateral agreement that let people secure their
data with the strongest possible encryption, using products that allow for the
recovery of plaintext by national authorities.
The key to legitimacy is that citizens will accept actions from their own
governments that they will not accept from others (particularly the U.S.)."
(emphasis added; the only way to safely do that is to use
an unbreakable frontdoor: anything vulnerable is a backdoor)
CSIS.org, 2016 (1962 think-tank for international policy institutions, Defense, and Security)
"Backdoor I think this kind of shady. Why wouldn't you want to go in the frontdoor
and be very public? We can create a legal framework for how we do this. It isn't
something that we have to hide." (emphasis added; unsurprisingly,
the NSA understands the problem – and its solution)
Admiral Michael
S. Rogers, Director of the NSA, Commander of the US Cyber Command, 2015
"There is a misconception that building a lawful intercept solution into a system
requires a so-called 'back door', one that foreign adversaries and hackers
may try to exploit. But that isn't true. We aren't seeking a back door approach.
We want to use the front door, with clarity and transparency, and with clear guidance
provided by law. We are completely comfortable with court orders and legal process –
front doors that provide the evidence and information we need to investigate
crime and prevent terrorist attacks." (emphasis added)
FBI director James Comey, 2015
"No one should be promising their customers that they will thumb their nose
at a US court order. They can promise strong encryption. They just need to
figure out how they can provide us plain text." (MLATs,
Mutual Legal Assistance Treaties, give full access to US authorities abroad)
Valerie E. Caproni, FBI General Counsel, 2010
"With regard to encryption, what law enforcement seeks is a balanced encryption
policy – one that puts strong, robust encryption in the hands of the general public
for legitimate uses, while at the same time providing not a back door,
but a Fourth Amendment front door, through which law enforcement can
walk with a court order when encryption is used for criminal purposes."
Charles Barry Smith, FBI's Chief of Digital
Telephony and Encryption Policy Unit, 2008
Since 2007, TWD has talked to the ENISA (European Union Agency for Network and Information Security), and presented it's provably-unbreakable frontdoor to many EU and national officials, Defense contractors, and industry leaders worldwide... not omitting the fact that Global-WAN's frontdoor is immensely more profitable for end-users and infrastructure operators.
Could it be that only US solutions can qualify?
That would explain why the so-called "European" PQCRYPTO's "Strategic Advisory Board members" lists Intel & MasterCard, why Daniel Julius Bernstein born in New York and Professor at the University of Illinois is "Project Lead", and why The Economist states that "PQCRYPTO's goal is not to find the most mathematically gnarly way of encrypting data, but rather to identify one that is sufficiently difficult to break". The goal is obviously to deliver yet another, a bit more subtly hidden, US-made backdoor.
Why is Europe outsourcing its infrastructure security to the USA? Because Western Finance and Intelligence Agencies, the ones deciding for the world, share similar agendas. At a cost: for the sake of spying and sabotaging, anything delivering serious security is eradicated – thanks to "the hidden fist that keeps the world safe for Silicon Valley's technologies".
Yet, the IoT and AI (Artificial Intelligence) will be cataclysmic failures if, because of the lack of any effective and durable security, anyone can remotely interfere with, infiltrate and sabotage any device and communication, everywhere, at any time:

"It's not the IoT devices themselves that will deliver the
biggest breakthrough – it's the ability to connect them to securely exchange
information and deliver it to users." (emphasis added)
Lockheed-Martin, "How The Internet of Things (IoT) Is Transforming Modern Warfare"
Lockheed-Martin, an US corporation, is officially the world's largest Defense contractor, but...

"What Lockheed Martin was to the 20th century, tech and Cyber-security
companies will be to the 21st."
Eric Schmidt, Google CEO (2013), quoted in "Assange: Google Is Not What It Seems"
Market capitalizations reflect Eric Schmidt's statement: Lockheed Martin is worth 8 times less than Alphabet (Google's holding). This is not surprising since "Google started with CIA and NSA research grants for mass citizen surveillance and tracking".
How much weight has "world peace and economic growth" as compared to "private historic
profits extracted from worldwide chaos"?
Not much when listed companies are in charge of the world's most important decisions
and have more weight than the FBI and NSA.
The problem is simple: the Foreign Policy historian Robert Kagan's "hidden fist" went too far.
TWD's Global-WAN ASIC microchips can provably-secure the world forever at a fraction of the price of today's governmental, academic, and industrial (ever-failing) "security theater"... but Google's CEO made it clear that Google, Amazon, Apple, Microsoft, Facebook, and the like all belong to the US military-industrial complex.
This is why independent vendors, like TWD, whatever their location, innovations, "talent" and "persistence" don't have the slightest chance in today's Western ecosystem. Not part of the problem, they can't either be part of the solution:
1. Create the problem, ("Cyber-security" decades-long investments called a "market failure" by The Economist)
2. Allow chaos to ensue, (backdoored security naturally leads to increasing disasters – amply reported by the media)
3. Offer a planned-obsolescent solution. (PQCRYPTO's backdoored security generously paid with public money is imposed)
Beyond nullifying competition, what other detrimental effects does this vicious cycle have on the World? Let's see.
Why the Defense contractors, Academia, and Silicon Valley want to preserve the
vulnerability of our common critical infrastructure?
To foster chaos & warfare: Defense contractors make money by selling
eye-wateringly expensive stuff to the military.
The closer to war the
world is, the higher Defense budgets are (and so is national debt, making finance
even more influent).
Ubiquitous backdoors have this magic effect of promoting the world to a state of constant war and chaos.
War is the parent of armies; from these proceed debts and taxes... known instruments for bringing the many under the domination of the few... No nation could preserve its freedom in the midst of continual warfare.
High government budgets turn into high corporate revenues which fuel (and justify)
lobbyism – to keep the same music playing.
"He who pays the piper calls the tune" (only the one paying the musicians can choose the song).
The want of parsimony, in time of peace, imposes the necessity of contracting debt in time of war.
How the US "Trusted" Tech Vendors are Selected?
Any group enjoying much larger powers than everybody else will eventually use it for its private interest. This obviously becomes unmanageable when these capabilities involve State powers because the State has then long ceased serving the "Common Good".
All this has happened a long time ago in Western countries: some US publicly traded companies are richer than the cumulated wealth of most nations (thanks to public money managed by private companies – including investment & pension funds – pouring people savings into the hands of a very few entrepreneurs celebrated as "geniuses" to justify their lavish lifestyle, extraordinary valuations, tax exemptions, subsides, public contracts, license to break the rules that all others have to respect, and huge losses immediately offset by new investments).
Even The Economist (with Google at its board) did not mince its words: (picture courtesy of The Economist)
"In Silicon Valley a handful of giants are enjoying market
shares and profit margins not seen since the robber barons in
the late 19th century." (emphasis added)
The Economist, "Robber barons and silicon sultans", 2014.
So Apple, Amazon, Facebook, Google and Microsoft (the only veteran still in the game)
do even better than the "silicon pioneers".
How profitable was this game exactly?
"The U.S. [DoD] has wasted over $14 trillion in fighting wars over the past 30 years rather
than investing in infrastructure at home. [...] The past 30 years, IBM, Cisco, Microsoft
– the profits they have made are much more than the four Chinese banks put together.
But where did the money go?
The U.S. is not distributing or investing its money properly, and that's why many people
in the country feel wracked with economic anxiety. Too much money flows to Wall Street
and Silicon Valley. [...] Globalization is a good thing, but it, too, should be inclusive,
with the spoils not just going to the wealthy few. The world needs new leadership, but
the new leadership is about working together."
(emphasis added)
Yahoo Finance,
"Chinese billionaire Jack Ma says the US wasted trillions on warfare" (2017)
Public-relation (PR) firms publishing sponsored posts prefer to refer to this process as the "deserved reward" of "merit" and "talent". Finance sometimes discretely invokes "Financial Darwinism": an "unnatural selection" done by massively transferring public money to a very few, hereby depriving all others from all possible investments, business deals, and jobs – the perfect self-empowering system.
Economists know very well what the consequences are:
- a very few are financed – at the expense of all others; (deprived from capital, firms can't hire staff and make products)
- the very few dominate the market with low-quality offers; (constant royal funding leads to abuse and self-complacentry)
- workers lack jobs because most firms lack customers; (chronically under-capitalized, they can't merely keep existing)
- most firms lack customers because workers lack jobs; (lifestyle is long gone, most fight to pay tax/energy/housing bills)
- the few celebrate victory while the economy goes belly-up. (when many go bankrupt, real-estate assets are a bargain)
At least it now clear where The Economist's "Cyber-security market failure" and the accelerating concentration of wealth come from.
In all the different employments of stock, the ordinary rate of profit varies more or less with the certainty or uncertainty of the returns.
Another classic economist tells us where the Central Bank QE policies are leading:
Given the distortions in monetary policy in the US, Europe and Japan since the acute phase of the 2008 financial crisis, Johan Wicksell [a Swedish economist, 1851-1926]'s insights are relevant for those seeking to understand how this economic cycle ends and the investment consequences which flow from the denouement.
For Wicksell, the "natural rate of interest" was the rate that causes savings and investment to broadly balance. It corresponds over the long term to an "equilibrium level", like the purchasing power parity exchange rate between two currencies. His other key measure was the "market rate of interest" which corresponds to companies' long term borrowing cost.
As Wicksell saw it, economic cycles tend to be driven by the spread between these two fundamental rates of interest. When the market rate is too low compared to the natural rate, the cost of capital is too cheap. The result will be capital misallocation, leading eventually to a decline in the economy's structural growth rate. In contrast, when the market rate is too high compared with the natural rate, capital is too expensive and an economy cannot grow. The result will be a bust, especially if overall indebtedness has risen sharply.
Is There Any Available Effective Solution?
All this illustrates how Western finance and military's selective perpetual funding, pressure on both the Internet ecosystem and the "rule of law", make it impossible for technically superior challengers to surface – or to merely survive – even in the US:
Twenty years ago, 600 companies were listed every year in the US (74 were listed in 2016). In two decades, the total number of listed US companies felt from 8,000 to less than 4,000. The FED's QE trillions have led into much less competition, not more.
China might insist to have a life of its own: it is often criticized by Westerners for its "unfair State-support for the Chinese industry". Since 2004, European Airbus has received the same accusation from Boeing and the US government. Copying the so-successful US business-model is certainly a major offense: treachery works best when you are the only one allowed to cheat.
As the largest world data collectors, Google, Amazon, Apple, Facebook, Microsoft, Uber, Airbnb, Tesla, eBay, etc. are the Western intelligences agencies' "symbiotic creatures" in an ecosystem where "Information is Power" (used to identify and terminate potential challengers before they can grow). No wonder why these Internet businesses are funded and protected like nothing else on Earth.
This explains the authorities' schizophrenia (security vs spying) but does not excuse the
blockage once the idea of a frontdoor has been brought to the table by the FBI, NSA and
CSIS
Center for Strategic and International Studies
Founded in 1962, CSIS is one of the world's
preeminent international policy institutions
focused on defense and security.
.
With TWD's mathematically-proven technology available and Government-validated since 2007, the claim by some "respected
independent experts" that such a solution is "technically infeasible" is groundless.
At this stage, the only remaining important question is: can today's Silicon Sultans' business-model be disrupted, let's say, for example, by making frontdoors immensely more profitable for end-users and infrastructure operators?
Yes: an universal unbreakable frontdoor like the one called by the FBI, the NSA, and the EU's Anti-Terrorism Coordinator would replace & disable today's ubiquitous backdoors. It would let national Intelligence Agencies do their work domestically – without having to compromise the world's critical infrastructure's (and end-users') security.
Provably-identified users and tech firms could no longer spread chaos, and the latter, to make money, would have to focus on delivering useful services to end-users. Excluding unauthorized backdoor exploitation would also stop the constant headlines shaming "compliant" users (equipped with security tools but left vulnerable).
As a bonus, a world without widely exploitable tech vulnerabilities would certainly improve, both socially and economically. Did I say already that Global-WAN's frontdoor is immensely more profitable for end-users and infrastructure operators?
Want to stay connected and nevertheless be safe – and at the same time generate huge recurring revenues?
Global-WAN provably-safe IDs and security shuts the door to all attacks, even the DDoS which have caused Internet blackouts for the six US largest banks, and the NYSE & NASDAQ in Sept. 2012.
Help us to manufacture plug & play
Global-WAN ASIC chips
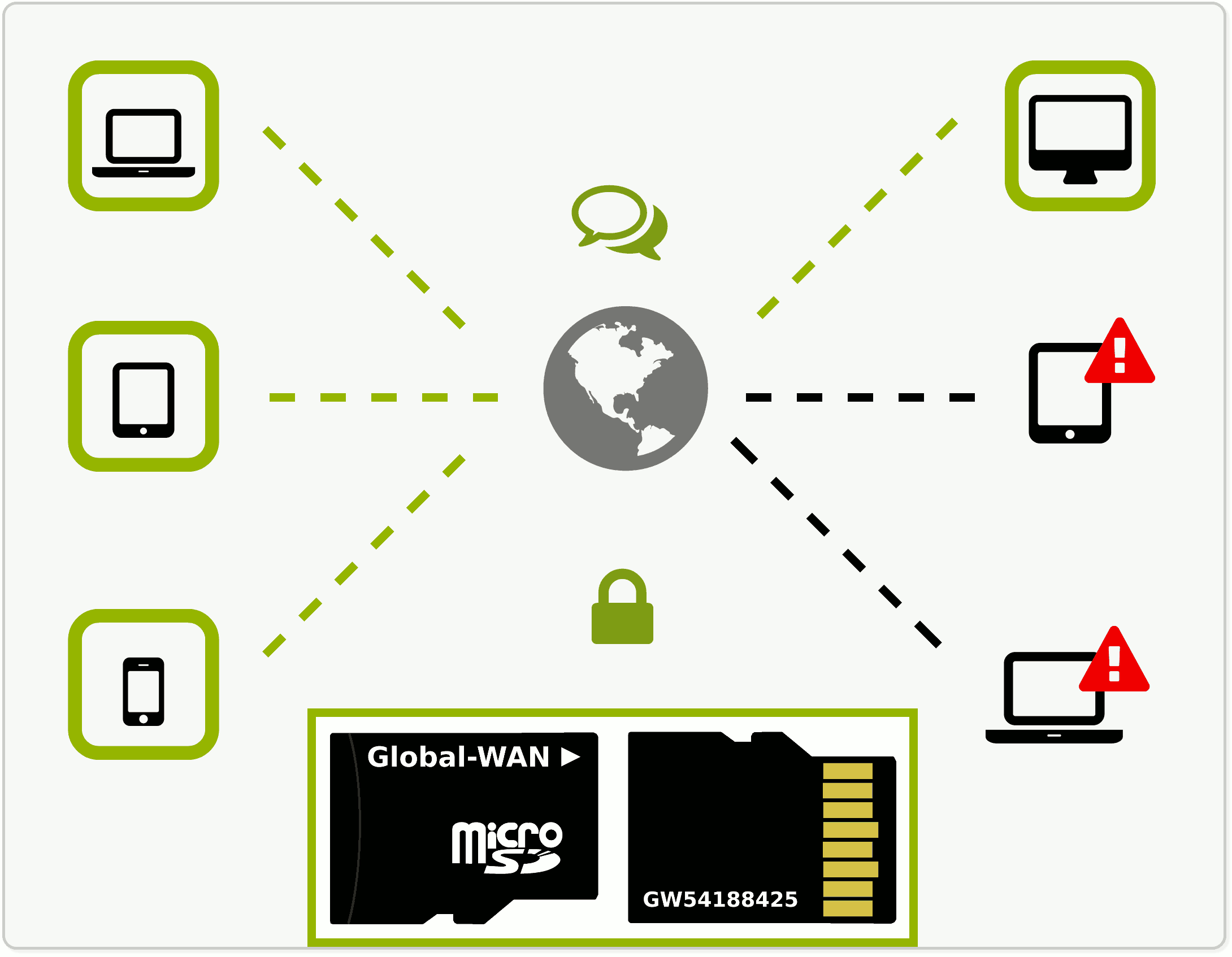 (for RFID tags, network cards, radios and modems)!
(for RFID tags, network cards, radios and modems)!
This will make it possible to deploy Global-WAN in your organization or even country-wide at ridiculously low costs (a few cents per unit!) and will let you sell your data at the price that you find appropriate – if you want to do so (data that can be stolen is free).
Large players such as multinational companies or government bodies can even license Global-WAN source code and deploy their own isolated version, which, in turn, can be bridged with your neighbors' regional Global-WAN, each side creating its own access permissions, without room for unwanted interference.
If there is any society among robbers and murderers, they must
at least... abstain from robbing and murdering
one another. So beneficence
is less essential than justice is to the existence of society; a lack of beneficence
will make a society uncomfortable, but the prevalence of injustice will utterly destroy it.
Adam Smith was a Scottish economist, philosopher, and author. He was a moral
philosopher, a pioneer of political economy, and was a key figure during the
Scottish Enlightenment era. He is best known for two classic works: "The Theory of
Moral Sentiments" (1759), and "An Inquiry into the Nature and Causes of the Wealth
of Nations" (1776). The latter, usually abbreviated as "The Wealth of Nations",
is considered his magnum opus and the first modern work of economics.
Smith's "invisible hand" states that, when individuals pursue their self-interest under conditions of justice ("free markets" and "fair competition" enforced by the "rule of law"), they unintentionally promote the "Common Good" (low prices, innovation, and diversity).
Adam Smith warned that a business-dominated political system would conspire against consumers and turn the economy into industrial monopolies and the politics into an oligopoly influencing legislation – in which case the "invisible hand" could no longer exist.