Theory vs. Practice
Diagnosis is not the end, but the beginning of practice.
"Unconditional" Security Requirements
According to Wikipedia, the "Security Theater is the practice of investing in countermeasures intended to provide the feeling of improved security while doing little or nothing to achieve it."
That helps to explain why The Economist wrote that cyber-security is a "market failure"... far before the chaos that we all see now.
Unlike "post-quantum" security relying on assumptions ("number-theoretical security assumptions", today's publicly-published quantum algorithms and the unreasonable hope that new quantum methods to break what is considered quantum-safe today will never surface), "unconditional" security is future-proof because it is assumptions-free.
These unpublished assumptions impact our daily life: Academia's formally-proven LTE "forgot" to feature packet integrity, like the formally-proven Wi-Fi "forgot" to verify the security of the protocol handshake. Both mistakes proved to be critical vulnerabilities... many years later.
The "Security Theater" is sustained by the varnish of respectability of a scientific community increasingly lacking credibilty:

A nefarious endlessly-funded rocket-scientist at work vs a naturally-gifted creature enjoying life.
Pick your poison.
Key-management is as important as data encryption because if you don't do it safely then your long-term secret encryption key will be compromised even before you start using it to actually encrypt data!
This is why, in this article, we will see what makes today's security standards fail and we will present the requirements to deliver "unconditional" security – in key-management (generation, storage, derivation, exchange) as well as in data encryption.
1. Key Generation
All CPUs, operating systems (Windows, repeatedly, and Linux, again and again), crypto libraries, and "security" products have long failed to implement true randomness generation for a simple reason – stealing the secret key is cheaper than breaking encryption (it is so attractive for governments that a NIST pseudo-random generator has been patented as... a "backdoor"):
If the algorithm is generating pseudo-randomness then an adversary can calculate in advance all the encryption keys that you will generate (including key-exchanges, initialization vectors, nonces, and PKI keys for SSL certificates used for e-commerce, e-banking, email/code/contract-signing, OS updates, remote administration, etc.).
The WebCryptoAPI used by Internet browsers relies on RtlGenRandom() on MICROSOFT Windows and the /dev/urandom device on Linux which are... pseudo-random number generators (PRNGs):
"The Crypto.getRandomValues() method lets you get cryptographically strong random values. The array given as the parameter is filled with random numbers (random in its cryptographic meaning).
To guarantee enough performance, implementations are not using a truly random number generator, but they are using a pseudo-random number generator seeded with a value with enough entropy. The PRNG used differs from one implementation to the other but is suitable for cryptographic usages. Implementations are also required to use a seed with enough entropy, like a system-level entropy source."
As, by definition, a PRNG is deterministic, there is NO WAY to use a "pseudo-random number generator seeded with a value with enough entropy" to generate "cryptographically strong random values" (you get only as much entropy as injected in the generator, that is, the size of the seed). If you hash a PRNG's output then you just create another deterministic PRNG.
As a result, when you see software claiming that they are "secured" by 'P2P Encryption' or 'Endpoint Encryption' (Internet browsers, Webmails, Messengers, File Transfers or Storage, etc.), "security" libraries, or "secure" protocols relying on these operating system or library APIs then it does not matter how safe the encryption algorithms are because, as explained above, the "secret" encryption keys are not so secret after all.
In contrast with the dominant (pseudo) "Scientific" claims that "not enough randomness can be extracted from a deterministic machine" (that's only true when you limit yourself to mouse-cursor moves and keyboard key strokes... which are mostly absent from servers), it is relatively easy to deliver true hardware randomness with a (traditional) deterministic computer and a procedural programming language like ANSI C by focusing on MHz/GHz high-frequency asynchronous events.
Yet, apart from us at TWD, I have never seen someone else's code doing that.
2. Key Storage
Keys should never be stored "as is" but rather calculated from different stored (and sometimes hard-coded) resources, including an input provided at runtime by the network, the keyboard, a serial port, etc. Even the procedure calculating the keys can be provided at runtime, and changed periodically, and be different for every user.
Any statically-stored key will be stolen, soon or later. And you don't want that if that's your keys.
This rule is equally valid for any identity, computer, electronic device, or... database.
3. Key Derivation (session keys)
With today's standards, if you are reusing your long-term secret key to encrypt data in consecutive sessions, then adversaries are able to reconstruct this key with only some of your ciphertexts.
To prevent this from happening people often use key derivation (KDF), generating session keys by hashing the long-term key with (pseudo-)random data.
With today's standards, unfortunately, this method is leaking long-term key bits. An adversary just has to collect this information to progressively reduce the key-space and finally recover the whole long-term secret key.
This is why many cryptosystem designs rather use key-exchange to use a new fresh key for every new session. Key-exchanges also let you keep a long-term private asymmetric key secret instead of having to share your secret long-term symmetric-key with your interlocutors (they could use it to impersonate you – or disclose it to third-parties – defeating the security of all your communications).
4. Key Exchange (session keys)
In today's "secure" protocols, public-key encryption is often used to authenticate and perform key-exchanges. For example, Bob encrypts his symmetric session-key with Alice's public-key and he signs this block to let Alice check that no MIM (Man In the Middle) attack is taking place (with such an attack an adversary would simply give Bob and Alice his own keys).
Here again, the devil is in the details: public-key encryption is provably-unsafe (the private and public keys are mathematically-related so one can be calculated from the other). It is supposedly difficult for the publicly-published state of the art, but a classified algorithm or device could do it and defeat the whole purpose of the exercise. With "unconditional" security available, it is obvious that if provably-weak algorithms are legally-enforced this can only be done to spy upon people.
Further, SSL certificates are also provably-unsafe: by definition, the "unique" signature generated by hashing Bob's profile will match an unlimited number of profiles (because the input profile is much larger than the fixed-size hash output). So, making a fake certificate does not even require an adversary to break the public-key encryption supposedly securing the hash value.
These are not theoretical issues: since at least 1999, the "Flame" malware has used a forged MICROSOFT certificate to infiltrate MICROSOFT Windows updates and inject malware in targeted computers.
For decades now, all "secure" biometric systems suffer from the very same flaw: only a few "reference" points are picked from an iris, palm, or fingerprint – and then a hash of these values is usually stored (instead of the few values themselves). As a result, spoofing someone's identity is immensely easier. Twenty-three years ago I have designed a short biometric signature suitable for database storage that is much safer while much smaller (so doing it right and more efficiently can be done).
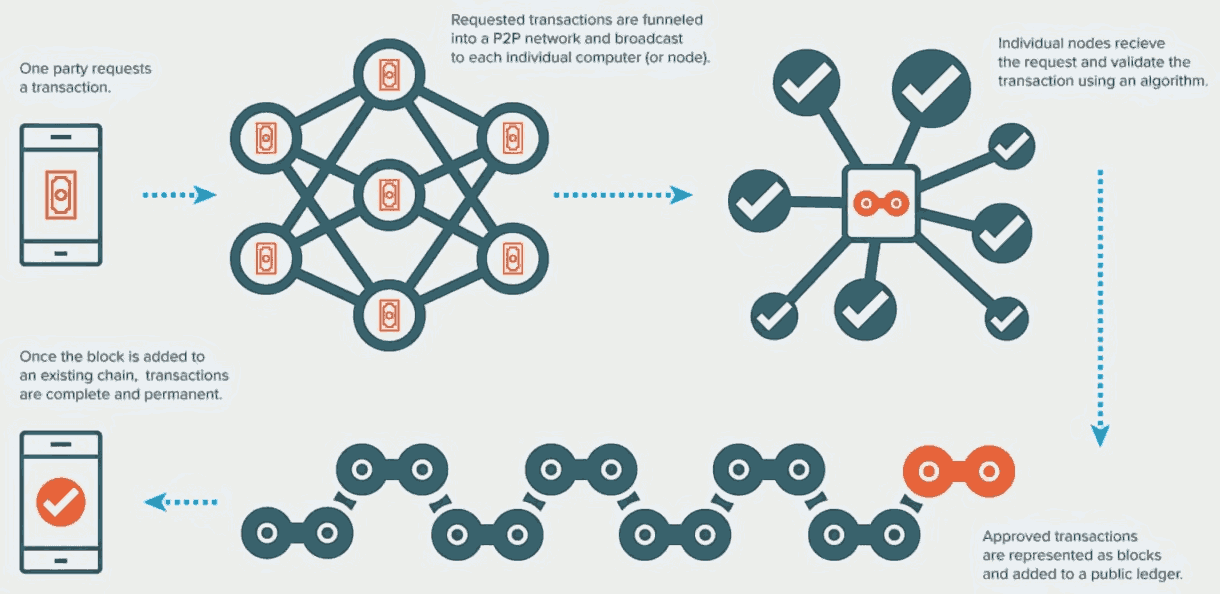
This is also why blockchains are unsafe by-design (even without consideration for the "consensus" scam where
an anonymous majority of two can bypass the transaction of one): an infinity of variable-length blocks has the same "unique"
32-byte hash. Blockchains could be made provably-secure, but this would require using security that is not designed to fail. Since 2009
several billions per year have been invested by banks, VCs, pension-funds, and universities in
provably-unsafe blockchains:
If you wonder why "Science", with its constant taxpayer funding worldwide for centuries, is so entrenched in well-understood technical "errors" then the answer is easy to find: generalized sick practices can only survive as long as money is involved to silence the voice of reason:
If you think, that only social sciences, law, history and literature are hijacked,
you did not pay attention. Think that mathematics and physics are free? Think again.
So, is it safer to update your OS or to leave it unpatched? Well, it depends on whether or not you are the only person able to reach and use it (remotely and physically) thanks to impenetrable security measures. Most users don't have the luxury to decide because they don't even suspect that there are State-sponsored wireless backdoors present in our computers' operating systems and CPUs.
Both kinds can – and should – be blocked: this 1972 US Army report
Click our link to download from our website this
report previously available from:
http://www.dtic.mil/dtic/tr/fulltext/u2/273787.pdf
Even if the US link above is later restored, the
PDF might have been edited – a very common
practice now, aimed at rewriting History.
presents animal and human experiments demonstrating the severe (and even deadly) health-damaging and cognition-detrimental
effects of the GHz radio-frequencies used today by our GSM/LTE phones, DECT residential phones, bluetooth game consoles and remote
controllers, Wi-Fi routers/TV-sets/loudspeakers, microwaves, emergency services, radios, radars, satellites...
A microwave oven operates at 2.45 GHz (a wavelength1 gigahertz (GHz) = 29.9792458 wavelength in centimeters (cm) of 12.2 cm – the antenna size) because this is the frequency for the resonance of a water molecule. This frequency is the most efficient to heat food containing water. Similar frequencies are used for Wi-Fi, bluetooth, wireless phones, etc.
Two Swiss academic studies
Haessig M, Jud F, Naegeli H, Kupper J, Spiess BM. 2009
"Prevalence of nuclear cataract in Swiss veal calves and its possible
association with mobile telephone antenna base stations".
Schweiz Arch Tierheilkd 151:471-478.
Hässig M, Jud F, Spiess B. 2012
"Increased occurrence of nuclear cataract in the calf after erection
of a mobile phone base station".
Schweiz Arch Tierheilkd 154:82-86.
have shown that pregnant cows grazing near mobile phone relays give birth to calves suffering abnormally high rates
of cataracts... despite the fact that fetuses are (supposedly protected) very deep in the body of the cow. The industry's claim that
microwaves only act in the surface of the body is clearly false.
"As the human brain's pineal gland does not distinguish between day-time light and electric fields,
"Resonance - Beigns of Frequency" scientific documentary
(melatonin: 1:14:35)
How radio frequencies kill bees, birds... and humans.
Research shows how frequencies control our mental and physical
health, synchronizes circadian rhythms, aids our immune system
and improves our sense of wellbeing.
This delicate balance has taken billions of years to perfect. But
over the last 25 years the harmony has been disturbed by artificial
frequencies.
the nocturnal cell-repairing processes (including cell-generated highly anti-oxidant melatonin hormone) are no-longer
taking place, severely imparing the immune system, and all cancers develop freely, caused by chronic DNA damage and oxidative stress".
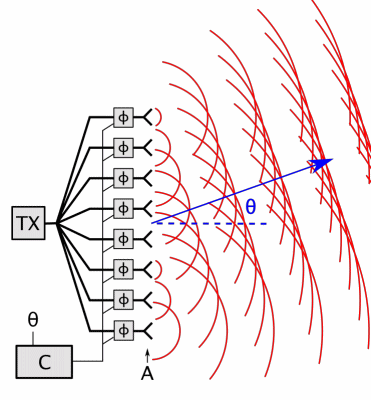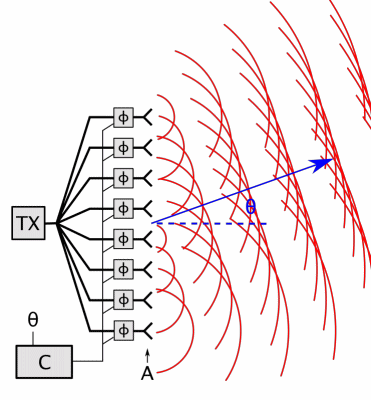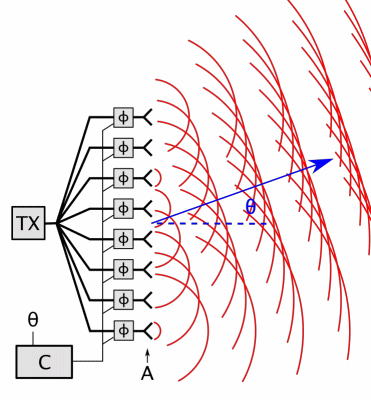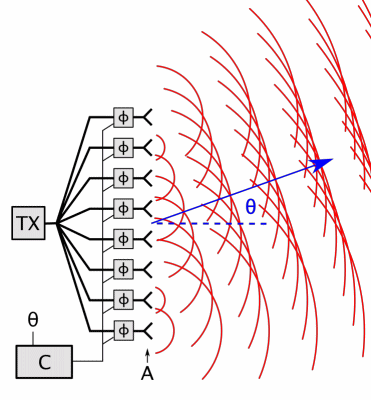
For 5G the US FCC (Federal Communications Commission) has approved the much higher frequencies used by radars, satellites and military systems, currently 24-48 GHz (1.25 cm to 6.2 mm) soon extended to 95+ GHz (< 3.2 mm). 5G antenas will be deployed every 100 meters on the street and in 25,000+ space satellites (nowhere to hide) with phased arrays (high-density antenna arrays) emitting highly pulsed (for data speed) focused beams (for directed energy) aimed directly at targeted receivers, and high energy outputs – designed to produce increased penetration to better traverse buildings, fog and clouds.
For some, that's just yet another occasion to take money from the taxpayer (this launch, started in February of 2018, will multiply today's number of satellites by a factor 11):
- SpaceX: 12,000 satellites (SpaceX and Tesla Motors belong to the same billionaire Elon Musk)
- OneWeb: 4,560 satellites
- Boeing: 2,956 satellites
- Spire Global: 972 satellites
The satellite lifespan will range from 5 to 10 years (causing recurring business for satellite manufacturers and launchers) and an army of 250,000 flying objects (planes, drones, balloons, etc.) will help covering more ground, giving long-term contracts to these Defense contractors.
5G is not just a 4G upgrade – it's a game-changer bringing new MILITARY radar and directed-energy capacities (as radio waves are absorbed by water – the human body acts as an antenna) aggravating by several orders of magnitude the well-known pathophysiological effects caused by non-thermal microwave frequency EMF passive exposure (home/office Wi-Fi hubs will cast 300-watt directed microwave beams 150 times stronger than 4G phones):
- Attack our nervous systems including our brains leading to widespread neurological/neuropsychiatric effects and possibly many other effects. This nervous system attack is of great concern.
- Attack our endocrine (hormonal) systems. The consequences of the disruption of these two regulatory systems is immense, such that it is a travesty to ignore these findings.
- Produce oxidative stress and free radical damage, which have central roles in essentially all chronic diseases.
- Attack the DNA of our cells, producing strand breaks in cellular DNA and oxidized bases in our cellular DNA. These in turn produce cancer and also mutations in germ line cells which produce mutations in future generations.
- Produce elevated levels of apoptosis (cell death), events especially important in causing both neurodegenerative diseases and infertility.
- Lower male and female fertility, lower sex hormones, lower libido and increased levels of spontaneous abortion and, as already stated, attack the DNA in sperm cells.
- Produce excessive intracellular calcium and excessive calcium signaling.
- Attack the cells of our bodies to cause cancer via 15 different mechanisms during cancer causation.
- Detrimental cardiac effects, dementias including Alzheimer's, ADHD and autism have also been scientifically-proven.
"What can I do?" you will tell me. Well, as a start you could replace your home Wi-Fi by cables and switch-off your smartphone as much as possible (especially by night), keep it away from your body whenever possible... and start questioning if all your family members really need one. You could also shield your home and offices (like banks, government offices, and datacenters do) with grounded carbon paint, shielding curtains, and coated windows. After all, the life of your kids is as important to you as the one of your nation's billionaires, bankers and politicians, right?
In a 2016 post, we have demonstrated that it is technically possible (and far more efficient) to make PKI provably-secure (by slightly altering its definition and relying on "unconditional" symmetric encryption) but using "unconditional" symmetric encryption can be done to deliver "assumptions-free" provably-secure key-exchanges without the PKI complications (and Certification Authority abuses).
Keeping a security framework simple and efficient has value: understood easily and implemented at a lower cost, simplicity also increases a cryptosystem's relevance on a wider range of hardware platforms (from RFID tags to datacenters for TWD's technology). In contrast, your car keys and credit cards may use lower-grade security because AES is too bulky to fit on many micro-controllers (and self-powered RFID tags are far less powerful than micro-controllers).
5. "Unconditional" Symmetric-Key Encryption
Today's standards, as we have seen, have many by-design issues that are technically-unnecessary if the goal is to deliver true security.
For centuries (at least 432 years now), it is well-understood (and publicly documented) how true security is weakened by complexity. Complexity is only necessary as a haystack to hide a needle (a secret State-sponsored backdoor). Hence the value of sabotating education in universities: the graduated "experts" are unable to understand the very basis of the "Science" they have learned.
"Computational" security (AES, SHA256) consists in rounds of defined arithmetic operations. People are using these functions as if they were perfectly random functions – which they are not (hence the security gaps). These symmetric-encryption and hashing functions generate ciphertext "domain-specific algebraic structures" that let adversaries reconstruct the algorithm and immensely reduce the key-space so it can be brute-forced, revealing a unique key and plaintext.
"Post-Quantum" security (NIST public-key candidates for signatures/key-exchanges, and AES with larger keys) is yet another backdoor, based on "number-theoretical security assumptions" (the reason behind today's public-key encryption standards replacement) and the hazardous hope that the "computational" security by-design flaws depicted above will stay secret forever.
This has recently been officially acknowledged by the UK government:
"Standards are soon rendered out-of-date by fast-changing threats and the frequent discovery of previously unknown
vulnerabilities" [... so we rather should] "anticipate fast-changing threats instead of slipping into a 'tick-box
compliance' with static standards." –
"Cyber Security of the UK's Critical National Infrastructure"
(Nov. 12th 2018)
UK Government's Joint Committee on the National Security Strategy
In a previous post we have presented the fundamental guidelines to deliver "unconditional" symmetric-key encryption – backed by indisputable scientific references (including Ron L. Rivest, the 'R' of "RSA"). Other perfect methods can be found in Claude Shannon's "A Mathematical Theory of Communication" (1948).
Once you have found how to deliver proven "unconditional" security you will need provably-secure ways to protect it against:
- random tampering (communication sabotage) without injecting any new redundancy (this would defeat the purpose of encryption which must absolutely stay a bijective transform to stay unbreakable);
- purpose tampering (secure protocol exploits) through known-plaintext attacks (which let an adversary modify parts of a ciphertext without having to break it) – on the top of the key-management issues explored above.
Having talked to many experts from Academia and the private-sector, it is clear that many of the areas covered in these three security-oriented posts are misunderstood – and often completely ignored. Instead of writing again and again the same things to my interlocutors, I wrote these documents in the hope that it will let a larger number of people take better decisions to protect their critical infrastructure (energy grid, water supply and treatment, telecoms, transportation, supply-chain, payment and settlement platforms, etc.).
A Last Word From "The Most Widely Acclaimed Security Expert In the World"
Bruce Schneier (son of a Supreme Court judge, ex-US Navy employee and NSA consultant) got far more exposure than his colleagues: his 1996 book "Applied Cryptography" was translated in many languages and received particular care from the marketing department.
It completely eclipsed another 1996 book titled "Handbook of Applied Cryptography
Free online at: http://cacr.uwaterloo.ca/hac/index.html
Unlike Bruce who advertises the link above on his website
I am advising you to stay away because the online version
has been edited to mislead people – especially about how
to achieve unbreakable encryption.
Who can believe that secretly rewriting history and falsifying
scientific books is done for the "common good"?
". Called "a major contribution to the field of cryptography"
by Ron Rivest (the 'R' of "RSA"), this scientific gem did not benefit from any marketing – nor it deserved translations.
I only discovered it at the end of 2017 – 21 years after its publication – when searching scientifically-established
facts and their related jargon for TWD's second government audit (made by cryptography experts with a mathematician background
– no computer-science involved).
Having read both I can tell you that my money and attention were miss-allocated (hijacked?) in 1996.
Why? They clearly serve opposite agendas. Let's quote Bruce's 1999 advices:
"Longer key lengths are better, but only up to a point. AES will have 128-bit, 192-bit, and 256-bit key lengths. This is far longer than needed for the foreseeable future. In fact, we cannot even imagine a world where 256-bit brute force searches are possible. It requires some fundamental breakthroughs in physics and our understanding of the universe. For public-key cryptography, 2048-bit keys have same sort of property; longer is meaningless.
Bruce's metaphysical posture was scientifically wrong:
Three years before Bruce's claims, the Grover's quantum algorithm (publicly published in 1996) advocated for symmetric keys to double in size from 256-bit to 512-bit to deliver 256 bits of "quantum-safe" security (due to BHT, this is not the case, by the way).
So, Bruce's 1999 recommendations were incorrect in 1996: enlarging AES keys beyond 256-bit matters – it's the difference between success and failure (says publicly Academia since 1996 about symmetric-key quantum-resistance).
What about Bruce's advice regarding public-key cryptography? To help application developers the US NIST published that:
1024-bit RSA keys are equivalent in strength to 80-bit symmetric keys | All RSA key-sizes are broken by
2048-bit RSA keys are equivalent in strength to 112-bit symmetric keys | quantum computers or by other classified
3072-bit RSA keys are equivalent in strength to 128-bit symmetric keys | ways able to factorize the large numbers
15360-bit RSA keys are
equivalent in strength to
This means that – to avoid introducing a weakness – 15360-bit RSA
keys should be used to exchange 256-bit symmetric keys.
This has never been done: 15360-bit RSA keys are too expensive
from a computational point of view (servers, micro-controllers)... and
introducing weaknesses in the security chain was the only goal
pursued by the NSA when founding the Verisign RSA spin-off.
So, Bruce Schneier's advice to use 2048-bit RSA keys creates a
security gap as large as most of the the necessary key-space:
2112 * 2144 = 2256
(but, when Bruce tells you to "trust the maths",
he is your friend, right?)
256-bit symmetric keys | used by the RSA public-key algorithm.
Oops. Bruce is wrong again when stating "for public-key cryptography, longer [than 2048-bit] is meaningless". Whether Bruce is incompetent or lying makes no difference: he misleads the world about what can make "computational" security "safe" for a few years (in contrast, future-proof "unconditional" security must rely on entropy rather than on mere arithmetic).
But, since the US Navy has paid his studies in cryptography, Bruce cannot be this much incompetent.
So, why did Bruce feel the need to deny established Science and even the NIST to blatantly lie about key-lengths?
Has he been secretly pursuing a clandestine disinformation mission that justified this so well-funded "unparalleled fame"?
This would explain a lot about his successful career as a conference speaker, university lecturer and as a writer at The Guardian...
on the top of his NSA-liaison role at BT (British Telecoms) to organize European, African and Middle-East interceptions.
Later, Bruce states that "longer key lengths are better, but only up to a point". As this statement contradicts the very basis of cryptography as a Science (Shannon) the only way to explain it is to recognize that the US NIST standards are defective by-design. In plain English, they are purposedly backdoored.
Here Bruce clearly suggests that these encryption algorithms might not be using all their key-space – and/or that a quick way exists to bypass a key-space brute-force search. He obviously already knew (before AES was publicly published) that:
- AES 256-bit can be broken without having to brute-force the whole 2256 key-space (thanks to quantum computers: Grover's, BHT and/or the AES "domain-specific algebraic structures" exploited on traditional computers; Note: enlarging AES keys won't protect against the latter!)
- public-key encryption is weak by-design due to its "number-theoretical security assumptions" – in the case of RSA, the alleged technical impossibility to factorize big numbers (quantum computers do that effortlessly but other ways work perfectly well on traditional computers).
Bruce knew all this but he kept the important information secret – and he lied to mislead people into believing that 1999 keys are "longer than needed"... in order to preserve the ability for the NSA to break all our encrypted communications.
This explains why he is seizing every single opportunity to spread fake information, to bury and denigrate trustworthy sources, as well as to promote edited versions of the so useful scientific book that his own (insights-free) book was in charge to eclipse.
Bruce's mission is and has always been to deceive people. Still not convinced? If you haven't done it already, read the tooltips by hovering dashed underlined text in this last chapter (links are dotted instead).
And, if you need to read it from the NSA directly, hear the NSA Director and Bruce Schneider (probably his passport name because that's the Bruce we know speaking on the video) saying on February 23, 2015, each at a few minutes of interval that, technically, security is "all or nothing".
Make no mistake: these recurring "errors", "omissions" and "misguidance" from the highest scientific and military authorities are of the same kind of the ones made by Academia when delivering fake "security proofs" about the LTE and Wi-Fi "secure" protocols that later proved to be State-sponsored backdoors.
Our taxpayer money funds these ubiquitous backdoors – like our CPUs' hidden features: remote control KVM, full access to system RAM, stealth access to network interfaces, embedded MINIX OS running custom applications, 3G SMS poison-pill, ability to run independently of the CPU... even if the device is powered-off.
Recent headlines boast about "quantum" breakthroughs (yet another backdoor, based on a fraud called "Quantum Physics theory"):
"ID Quantique [a Swiss company funded by the US] has been selling hardware for BB84-type protocols, since 2004 and claims that its quantum cryptography provides 'absolute security, guaranteed by the fundamental laws of physics'.
However, Vadim Makarov has shown that the ID Quantique devices are vulnerable to control by attackers, that various subsequent countermeasures are still vulnerable, and that analogous vulnerabilities in another quantum-key-distribution (QKD) system are completely exploitable at low cost.
The most reasonable extrapolation is that all of ID Quantique's devices are exploitable."
Daniel J. Bernstein, Head of the http://pqcrypto.eu/ public/private R&D project
Software security is pointless in such an environment – yet "compliance" carefully preserves access to the backdoors, and even mandates their deployment. This is what "deception" is for: make people unable to understand the nature of the threats.
Security is too serious to be left to government employees (Academia, Defense, etc.) because "It is difficult to get a man to understand something when his salary depends on not understanding it." – Upton B. Sinclair (1878-1968).